There are no bad teams only bad leaders and by corollary the success of a leader is directly attributed to the performance of their team. Now, a good leader can change the performance of a team from bad to great, but I’m getting ahead of myself. Let’s talk about building a security team and how to think about it.
First, it is rare for a leader to join an organization with a blank slate unless they are joining a very early startup. Most organizations will have some if not all parts of a security function and so a leader may need to assess if the existing org structure is meeting the needs of the business. In my particular case, I inherited a very small, flat security organization and it effectively allowed me to start from scratch.
What type of people does a security org need?
In general, a security org needs the following archetypes:
- Builders – these are people who create things and are your engineers, product and application security specialists, devsecops folks, etc.
- Defenders – these people find weaknesses and help protect against them. They are your security operations people, red team, blue team, physical security, threat intel, researchers and threat hunters.
- Thinkers – folks who think about where the industry is going, what capabilities are needed, what policies and standards are needed, etc. They are your architects, governance, legal, privacy and security leadership at all levels.
- Cat Herders (Organizers) – your organization may or may not need people to help organize, validate and keep things on track. If you do, these are your scrum masters, program and project managers, auditors, risk and compliance people.
In my experience, a security organization will ultimately be structured as a reflection of the broader organization. What do I mean by that? If your broader org has separate legal, IT, sales, development, finance, hr, etc. orgs then generally you will need unique parts of your security organization to interact with each of these larger parts of the organization. Similarly, the maturity of the broader org will also influence how your organization is structured. If your IT group doesn’t have an accurate asset inventory or has poor hygiene around patching, posture, etc. then you may need to have a security function to augment this group until they come up to par.
In my particular case I started out with three groups – engineering, operations and governance and risk. I eventually added compliance, program management, product security and privacy and this model scaled really well up to a point (which I’ll talk about in a later post).
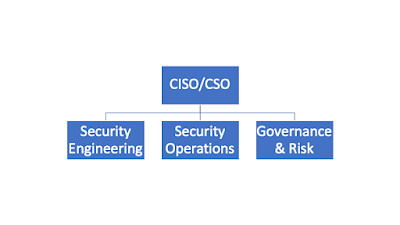 |
| Initial Security Org |
 |
| Later Security Org |
I was fortunate to have very supportive leadership that allowed me to hire and grow the team aggressively and this was one of the contributing factors in how I was able to reduce risk to the business by over 70 percent in 3 years.
If you are curious how to structure a security org Henry Jiang produced an excellent chart of all the different domains in cybersecurity. You can find it here.
I use this chart a lot in my current role to explain to people what a comprehensive organization should include. You don’t have to structure your org this way, but somewhere in the business someone should be performing the function and be accountable to security.
Ultimately, as a CSO/CISO people are not only your weakest link, but they are also your most valuable asset. The performance of your team and their ability to achieve results within the broader org is critically important to being able to manage or reduce risk to the business. People are the first and most important factor that allowed me to achieve the results I mentioned in my first post.
Up next, we will talk about creating a strategic plan.

One thought on “Security Team Assemble!”